
How two very different attack types exploit gaps in security, compliance, and financial workflows.
Most organizations treat "fraud and phishing protection" as a single line item in their security budget. But these are fundamentally different attack types and conflating them can create dangerous gaps in your defense posture.
Phishing is a sprint. It targets an individual and hits like a lightning strike, relying on a moment of confusion or misplaced trust. Fraud is a marathon. It builds like a flood, slowly through patterns, relationships, laundering paths, and coordinated networks that exploit gaps in systems over time. Fraud is a submarine, stalking the depth undetected for weeks. Phishing is a 30-seconds-to-impact torpedo alarm.
And just as it takes a three-way mixed metaphor to explain the difference between fraud and phishing, institutions need a different mix of tools and controls to detect and prevent both.
Phishing is a human and interface attack. The goal is to manipulate a person into granting access or authorizing something they do not intend. Phishing aims to break trust at the point of interaction. Common phishing vectors in Web3 include:
Phishing almost always aims to achieve one of three outcomes: (1) Steal a credential or session; (2) Trick someone into signing an approval that looks harmless; (3) Redirect funds to an attacker-owned destination. In other words, phishing is an access attack. The damage happens only after a human has been fooled.
Phishing succeeds through urgency and technical obscurity. Users are pressured to act quickly ("limited time offer," "claim your airdrop now") and can't easily verify what a transaction will actually do before signing it.
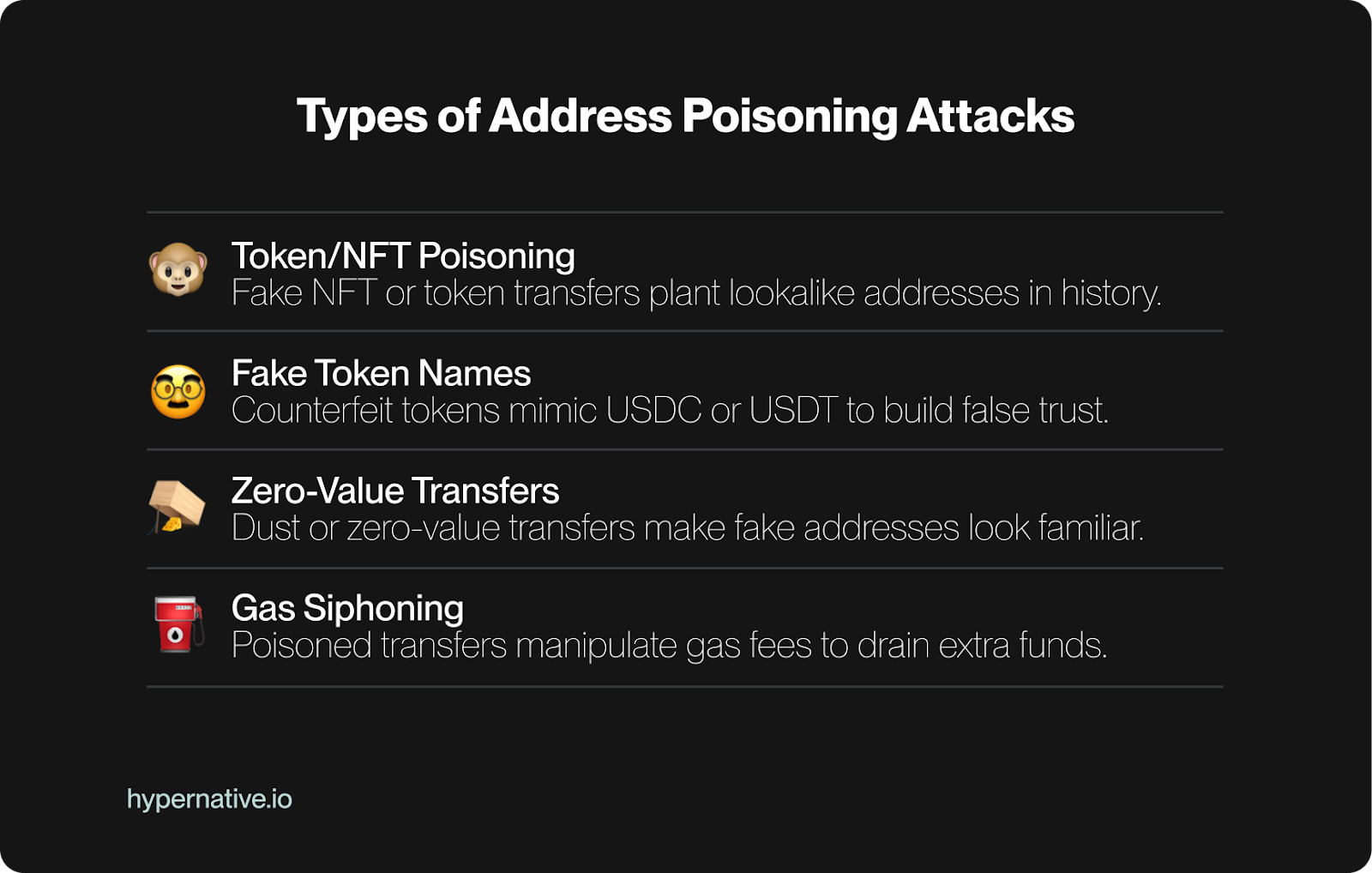
Fraud is a financial and transactional attack. While phishing harvests approval by tricking the victim into transferring funds, victims of fraud do so knowingly, thinking the recipient of the funds is legit. Fraudsters build networks of mule accounts, laundering paths, and cross-chain routes designed to extract and move assets.
Examples include:
Fraud does not require the victim to make a mistake. It exploits gaps in transaction controls, screening, and policy enforcement. This makes fraud a systemic risk for institutions. It affects treasury operations, employee workflows, listings and settlements, payment paths, liquidity management, and compliance exposure.
Fraud operations don't announce themselves. There's no malicious smart contract to analyze at the moment of deception, just a series of seemingly normal transactions that, when analyzed together over time, reveal a coordinated scam operation.
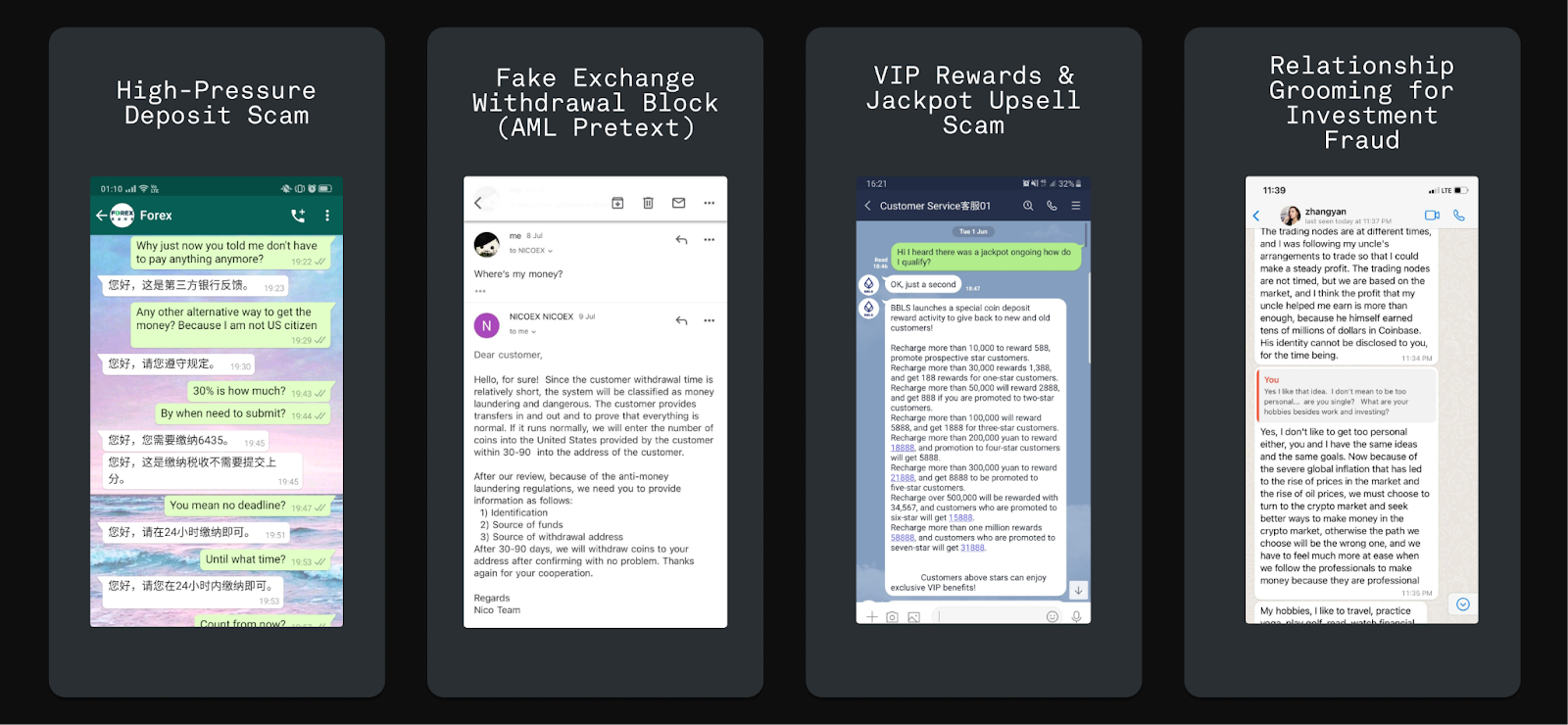
Preventing phishing from hitting its target requires controls aimed at users, identity, and interfaces. Organizations need the ability to detect malicious intent before the user interacts. Effective phishing defense requires:
Stopping fraud calls for controls aimed at transactions, counterparties, and financial flows. Organizations need the ability to evaluate risk before funds move. A solid fraud defense includes, but is not limited to:
Hypernative delivers a unified, proactive, and predictive defense against both phishing and fraud by focusing on real-time intelligence and pre-transaction prevention. Our solutions reflect the fact that sophisticated institutions require specific tools for their separate Fraud and Security teams.
Hypernative’s Fraud Prevention solution is engineered specifically for Risk and Fraud teams who need to stop the marathon of social engineering schemes like Pig Butchering and Investment Scams, where the user willingly initiates the transfer.
Hypernative identifies coordinated scam operations by continuously scanning the blockchain to map dynamic “fraud clusters.” Our proprietary ML models, which incorporate unique fraud signals, consistently uncover millions in previously undetected fraud. When a withdrawal is initiated, our Fraud Screener API provides a real-time recommendation (Approve/Deny) along with a severity level and justification based on the recipient's connection to these clusters.
This solution is designed for Fraud Teams and provides the critical time needed to intervene and prevent losses before settlement, securing both customer funds and institutional reputation.
Hypernative’s solution suite for wallets and security teams, including Wallet Protect and Hypernative Guardian, provides layers of defense at the point of interaction to stop the sprint attack that tricks a user into signing.
To protect retail users, our Wallet Protect solution offers:
For institutions, our Hypernative Guardian solution includes all the capabilities above but adds the concept of automated approval/denial functionality based on configurable, internal policies, making it the preferred choice for institutional treasury and risk operations requiring programmatic control over transaction execution.
Reach out for a demo of Hypernative’s phishing and fraud prevention solutions, tune into Hypernative’s blog and our social channels to keep up with the latest on cybersecurity in Web3.
Secure everything you build, run and own in Web3 with Hypernative.
Website | X (Twitter) | LinkedIn