
When security depends on copy-paste, even small mistakes become catastrophic.
Look both ways before crossing the street. Don’t talk to strangers. Never copy anything from Etherscan. These are the three lessons every parent should pass down to their crypto-native kids. Hidden among legitimate addresses in your transaction history are poisoned lookalikes that trick users into sending funds to attackers. One routine copy-paste and your college fund is on a one-way trip to a Russian exchange.
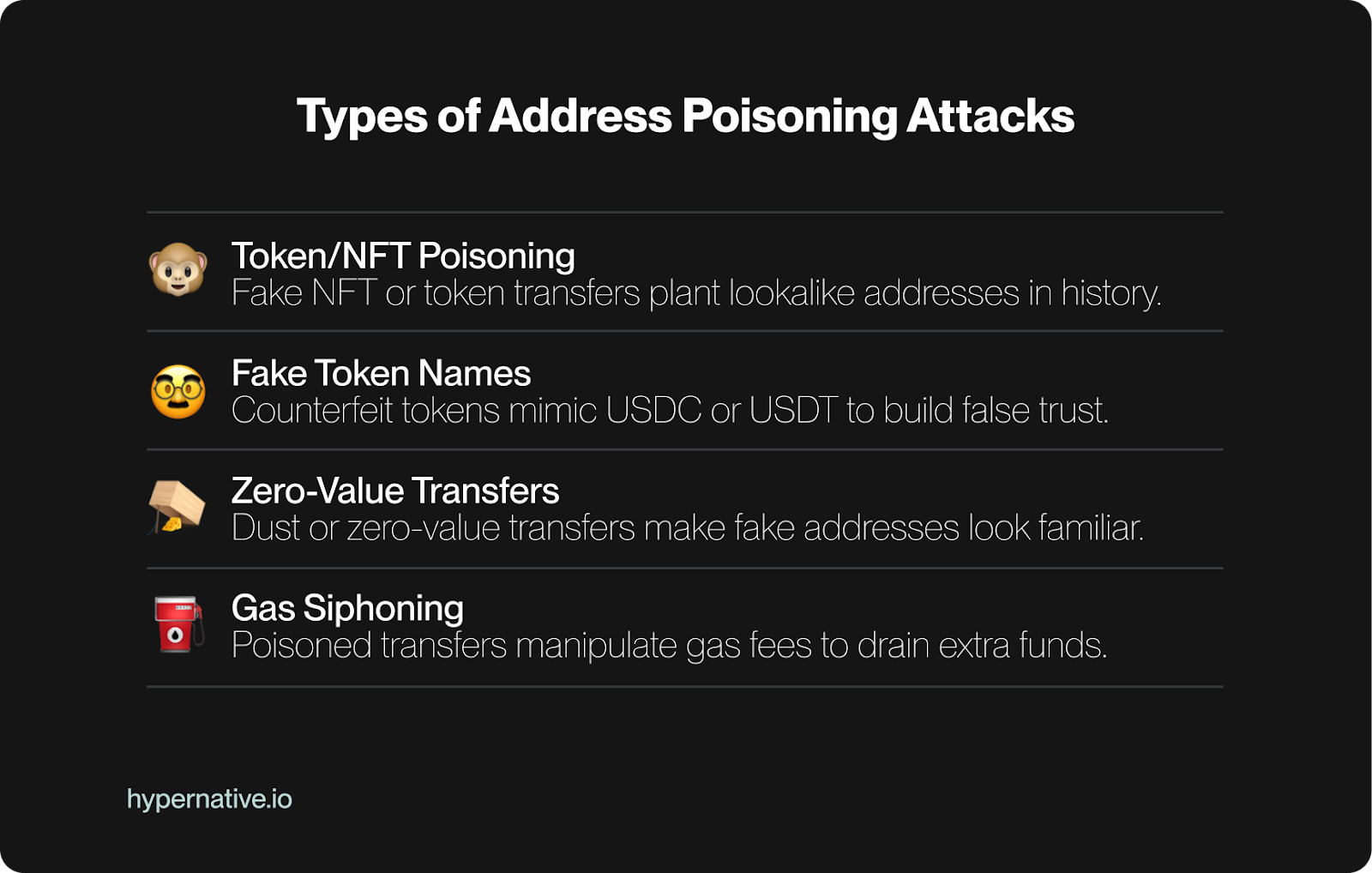
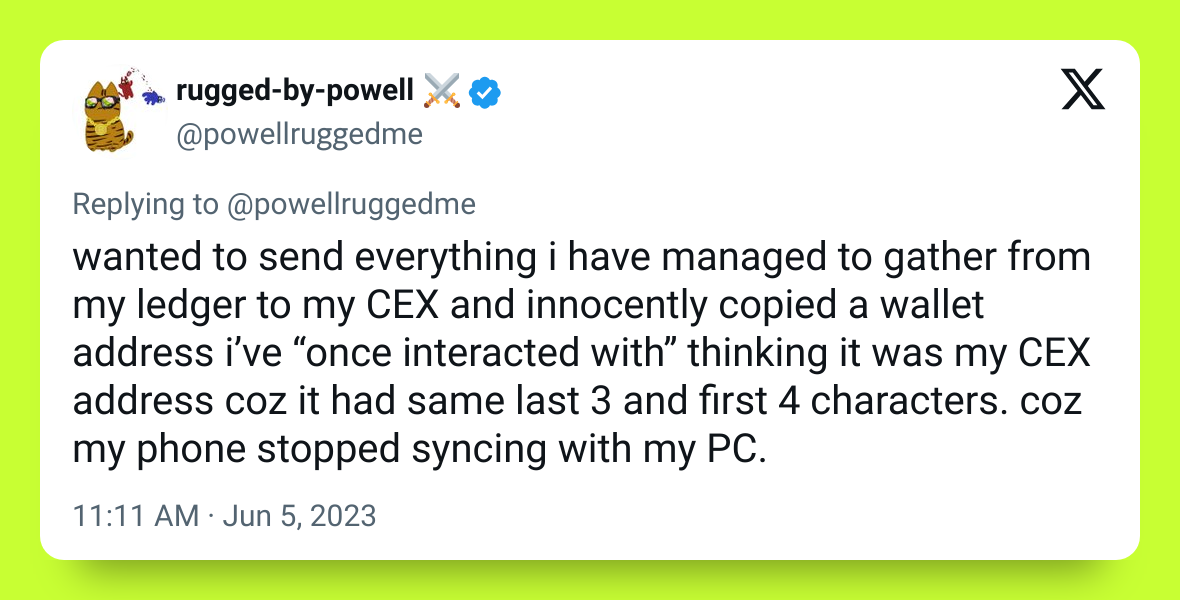
Address poisoning works by inserting fake, lookalike wallet addresses into your transaction history. Attackers send small, meaningless transfers to your wallet using an address that mimics one you’ve interacted with before. Because most wallets only display the first and last few characters of an address, the poisoned version looks almost identical to the real one. When you copy from your history and paste it into a new transaction, you may end up sending funds to the attacker instead of the intended recipient.
In the gallery of Web3 exploits, address poisoning looks almost laughably simple. It lacks the technical sophistication of flashloan attacks, the criminal infrastructure of wallet drainers, or the social engineering of phishing campaigns. What it exploits instead is harder to patch: human fallibility. The quick glance at the first and last characters of an address feel safe but often are not. That reliance on shortcuts makes poisoning powerful. Sometimes the most effective attack is the one aimed at our own habits.
For wallets, the danger is bigger than a single user mistake. Every poisoned transaction that slips through erodes trust in the wallet itself. Users rarely blame the attacker they cannot see. They blame the interface that showed them a fake address and gave them no warning. That reputational risk makes address poisoning more than a nuisance. It is a systemic blindspot that weakens adoption and undermines the credibility of Web3 applications.
Legacy wallet defenses were never built for attacks like address poisoning. They rely on static blacklists and heuristic rules, which only stop threats that have already been identified. New, poisoned addresses are generated on the fly, making blocklists useless. Heuristics can sometimes catch variations of known scams, but they are constrained by the foresight of their creators and prone to false positives.
Even when these defenses work, their scope is limited. Very often the fake transactions are automatically generated and real time detection is critical: in some scenarios the user is expected to transact seconds or minutes after previous interactions and without a real time block level update of the fake addresses the user is left exposed.
Most existing defenses also only monitor a slice of onchain activity, often missing non-EVM chains. The result is a narrow field of vision: wallets see only part of the threat surface, while attackers exploit the blindspots. This is why address poisoning, despite its simplicity, slips past legacy defenses and puts both users and wallet providers at risk.
Wallet providers don’t have to fight this battle alone. The building blocks already exist in the form of battle-tested security approaches pioneered with institutions that can, and now should, be adapted to consumer wallets. What matters is applying these protections at the speed of Web3.
It starts upstream. Poisoned addresses don’t appear by magic at the moment of transfer; they are seeded onchain ahead of time through dust transactions, fake tokens, or spam NFTs. Continuous monitoring of contracts, tokens, and infrastructure is the first line of defense, surfacing these malicious entries the moment they are deployed. Wallets that can tap into this intelligence don’t just leave users to sort through cluttered histories, they prevent poisoned addresses from ever being mistaken for legitimate ones.
At the point of interaction, that intelligence must become clear, actionable defenses. Hypernative Wallet Protect does exactly this. It simulates transactions before they execute, checks outbound assets for malicious tokens or spam, assesses dApp and URL reputations, and delivers consistent protection across chains. By continuously monitoring for new fraud patterns and flagging anomalies, Wallet Protect closes the blindspot that allows address poisoning and other scams to succeed. In short, wallets must evolve from signature tools into intelligent security layers that adapt in real time and earn trust with every interaction.
In our upcoming webinar, Hypernative CTO Dan Caspi and VP Strategy Marshall Lipman will explore how these threats unfold in practice and what wallets can do to stop them in real time. Mark your calendars for Sept. 25 and save your seat by registering here.
Reach out for a demo of Hypernative’s solutions for wallet providers, tune into Hypernative’s blog and our social channels to keep up with the latest on cybersecurity in Web3.
Secure everything you build, run and own in Web3 with Hypernative.