
Why both staking operators and yield platforms need to adopt real-time controls and embed transaction-level safeguards into every flow.
Update Sept. 13, 2025: This transaction had set the withdrawal authority on Aug. 31, which would have limited potential actions to secure the funds.
On Sept. 8, SwissBorg suffered a major exploit that resulted in the theft of 192,600 SOL tokens worth $41.3M across 8 malicious transactions.
SwissBorg, a leading European wealth app, offers customers an Earn product, a way to deposit funds and earn yield via staking. To power this, they rely on Kiln, a professional staking operator managing deposits and withdrawals of staked funds.
Kiln’s infrastructure was compromised several days prior, allowing the attacker to manipulate stake account authorities and prepare for theft without triggering immediate alarms.
Sept. 4, 2025: First Signs of Intrusion
The attacker experimented with both authorize and authorizeChecked instructions on a SwissBorg/Kiln stake account (example). This suggests the attacker was testing methods to escalate control, indicating uncertainty about how to best exploit the accounts.
Sept. 6, 2025: Coordinated Authority Changes
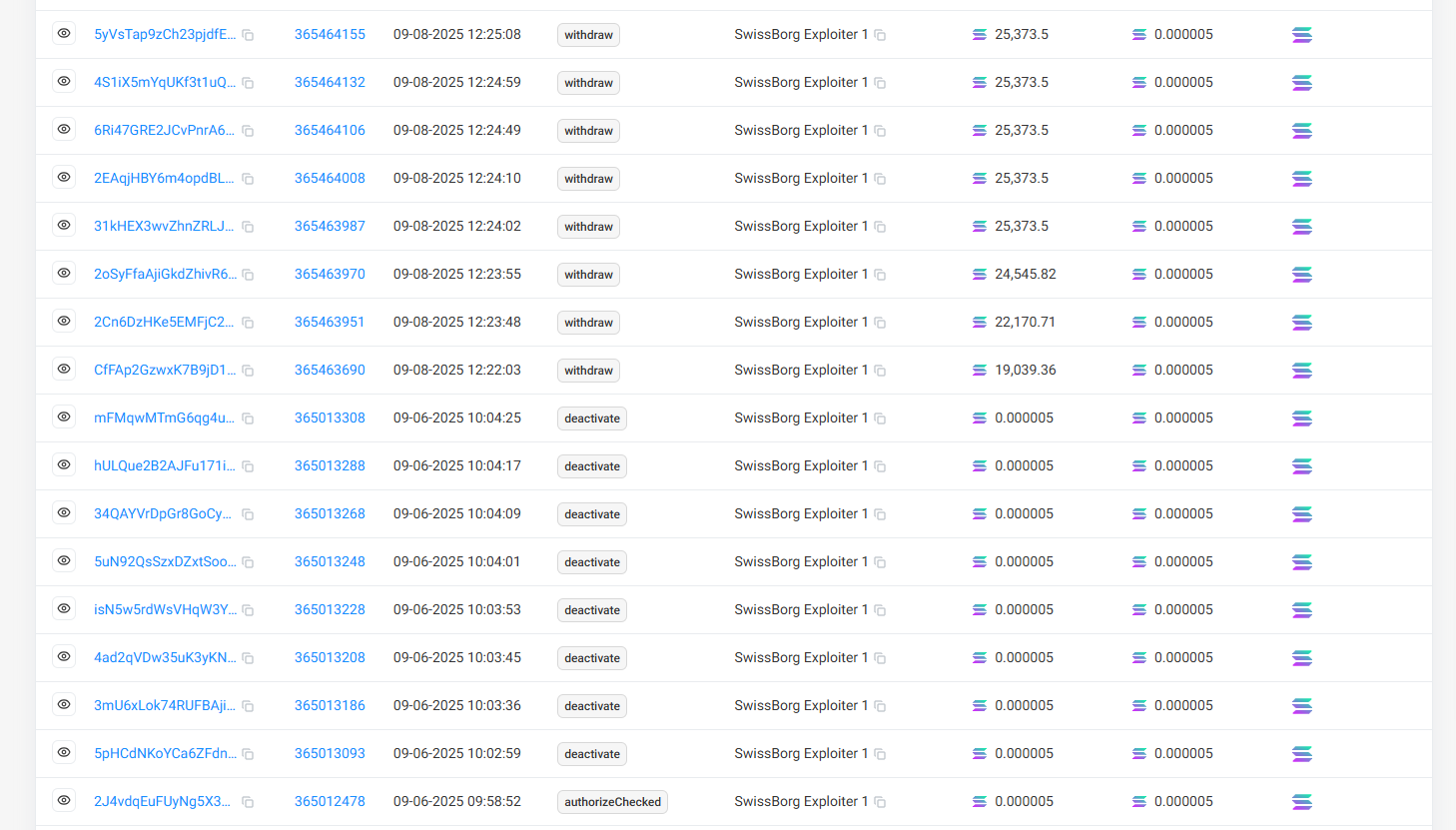
Two days later, the attacker executed eight authorizeChecked calls, one for each victim Stake Account. Importantly, in every call, the attacker changed the Staker authority.
Sept. 8, 2025: Exploit Executed
At 12:22:03 UTC, withdrawals began (first transaction). Over the next 3 minutes, the attacker drained 192,600 SOL across 8 withdrawals. Even reacting after the first withdrawal it would have been possible to save over 80% of funds.

Operators, who construct and submit transactions, are the first line of defense:
Services act as custodians of customer funds and depend on operators. To stay secure, they must ensure:
This incident highlights two key truths for staking ecosystems:
The SwissBorg exploit wasn’t inevitable. The early authorizeChecked activity gave more than enough time for defenders to intervene. With Hypernative Guardian and Platform, both operators and services can detect these anomalies, deny malicious transactions, and respond in time to save customer funds.
Hypernative turns attacker “signal” into defender action, protecting staking ecosystems from supply-chain compromises.
If your team is reassessing its security posture, we’re here to answer questions and show how real-time protection can prevent the next incident. Reach out for a demo of Hypernative’s solutions, tune into Hypernative’s blog and our social channels to keep up with the latest on cybersecurity in Web3.
Secure everything you build, run and own in Web3 with Hypernative.
Website | X (Twitter) | LinkedIn