
As malicious actors grow more sophisticated, Web3 projects must embrace a security posture that spans audits, real-time monitoring, operational security, and post-incident response planning
All technologies tend toward invisibility on their path to mass adoption. Nobody thinks about TCP/IP, server stacks or the power grid anymore—we just tap, swipe, and stream. Blockchains are heading the same way, and with that comes a set of security misconceptions that thrive when complexity is out of sight.
Misconception #1: Security audits are enough
Misconception #2: Attacks happen in a single transaction
Misconception #3: Funds are lost once under attack
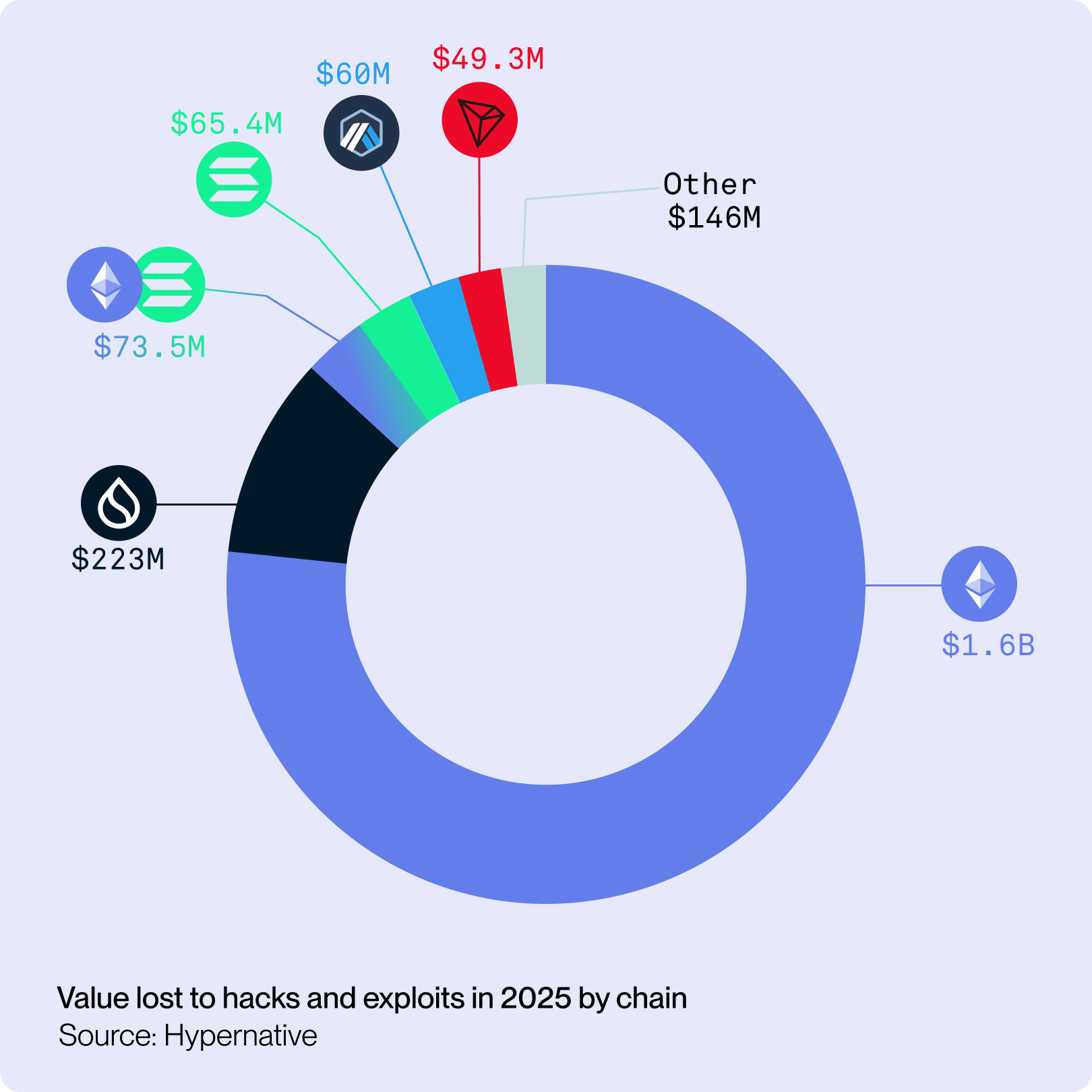
These misconceptions cost Web3 projects more than $2.21B in funds lost to hacks, exploits, rug pulls, and private key compromises so far this year, according to data collected by the Hypernative platform. For comparison, total losses in all of last year were $2.2B—meaning we are on track to exceed that mark just over halfway through 2025, a clear sign of how rapidly attackers are evolving. Defending against increasingly sophisticated attackers requires Web3 projects to adopt a comprehensive security posture—one that includes audits, real-time monitoring, operational security, and post-incident response planning.
For many Web3 projects security starts and ends with a smart contract audit. Among the incidents detected by Hypernative where the loss exceeded $1M, 77% of the projects had at least one audit and 57% had two or more.
While audits and bounties are necessary, they alone are not enough. The real battle begins after the audited smart contracts go live, and that's where monitoring solutions come into play. The evolving nature of blockchain technology requires continuous vigilance and there is no substitute for proactive monitoring of emerging threats.
Another common misconception in Web3 is that hacks happen all at once, like a strike of a lightning. The reality could not be further from the truth, as exploits typically progress through four stages: funding, tooling, attack, and cashing out. The transparency of blockchain networks makes each of the steps detectable thanks to monitoring tools like the Hypernative Platform. If you can see it, you can stop it.
About 45% of the incidents where the root cause was an onchain exploit or hack, involved more than one execution transaction. Of those, 82% unfolded over more than 2 transactions, giving monitoring tools ample time to detect the threat and initiate a response.
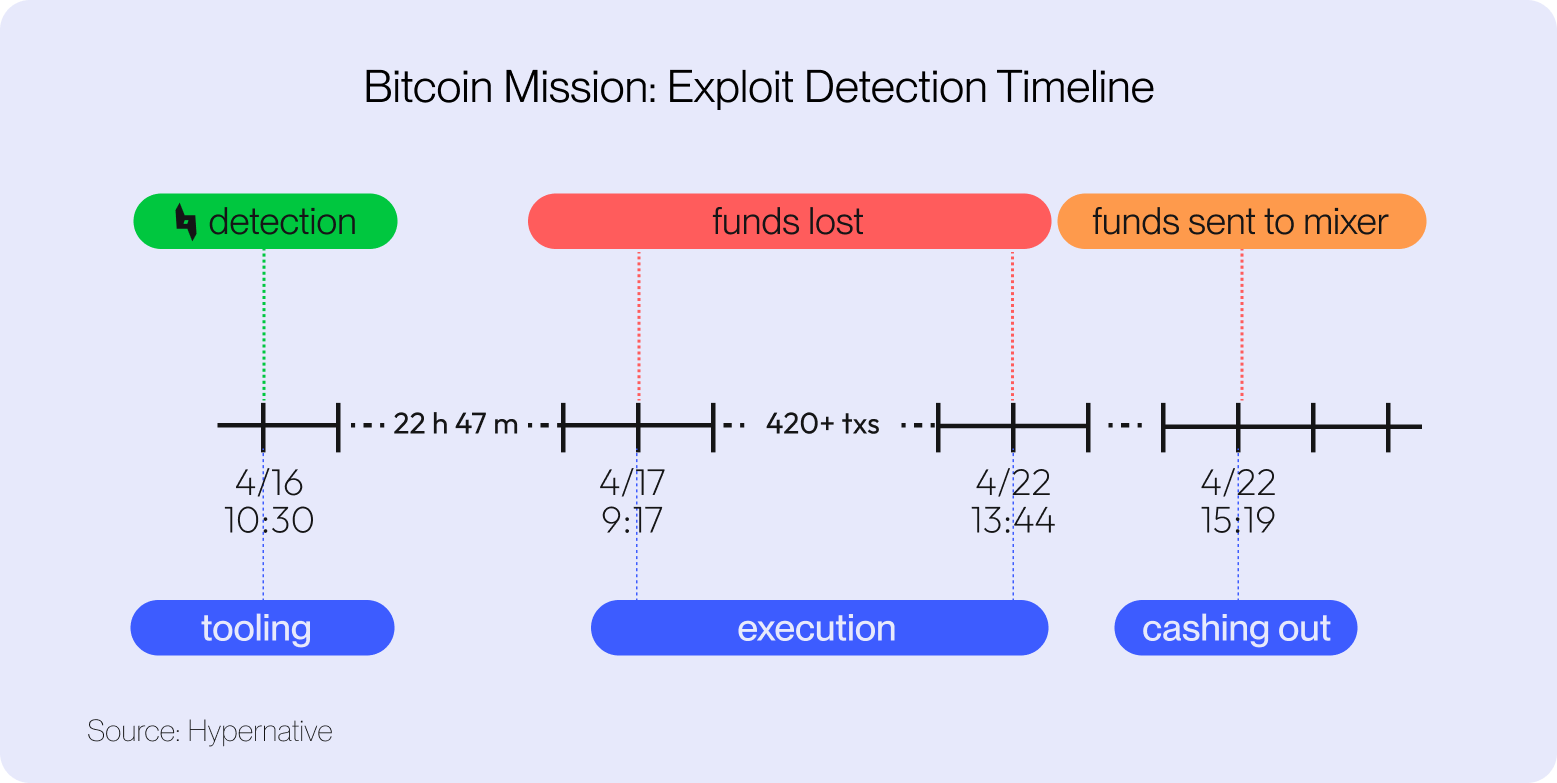
Read more: Hypernative Detection: $1.3M Exploit of Bitcoin Mission on Arbitrum
When the unthinkable happens, each minute counts and having a playbook ready can make the difference between a flesh-wound and a disastrous loss. A comprehensive incident response plan can help you navigate security incidents, mitigate damage, and secure your assets. The good news is that you probably have more time to respond than you think.
In 62% of the cases when an onchain exploit or a hack was involved, the time between the first detection and the first exploit transaction was 1 minute or more, and in 32% of the cases more than 5 minutes. The median elapsed time was just under 2 minutes -- not enough time for human-in-the-loop reaction, but more than plenty for automated failsafes.
Read more: How Kinetic Stopped a Hack and Saved $5M With Hypernative
New technology only delivers on its promise when paired with new ways of working. Just as factories had to rethink their entire layout to benefit from electricity, Web3 projects need to rethink how they approach security to fully realize the value of blockchain technology.
Gal Sagie
Co-founder & CEO @ Hypernative
That rethink starts with real-time monitoring. If audits were the security standard of the last era, continuous, context-rich observation is the foundation of what comes next. The checklist below outlines what modern monitoring should look like: what to check, what to ask, and why it matters.
What to Check: Ensure you are observing all onchain and offchain activities—constantly.
What to Look For: Ask your provider what’s included in their coverage. A comprehensive setup should monitor smart contracts, transaction events, governance proposals, wallet interactions, price feeds, Web apps, governance sites, and public vulnerability databases.
Expert Insight: It’s not enough to just watch your own stack. A strong monitoring program surfaces ecosystem-wide threats that could impact your protocol or assets, even if the exploit begins elsewhere.
What to Check: Ability to detect abnormal patterns in execution logic or wallet behavior.
What to Look For: Look for systems that go beyond static signatures to identify intent-based anomalies like unexpected token approvals, abnormal contract upgrades, or new behaviors from known entities.
Expert Insight: Many attacks don’t look malicious at the code level. Detecting behavioral anomalies is key to catching novel exploits before they go mainstream.
What to Check: Real-time notifications for any high-risk activity or security-relevant event.
What to Look For: Alerts should be fast, actionable, and integrate seamlessly into your ops stack—Slack, Telegram, PagerDuty, Webhooks, email, etc.
Expert Insight: Speed is everything. A well-timed alert, especially one that includes context, can mean the difference between reacting in seconds versus suffering a multimillion-dollar loss.
What to Check: How well monitoring integrates with other security efforts—audits, bug bounties, internal controls.
What to Look For: Strong platforms don’t operate in silos. They enhance your existing processes, providing layered coverage and visibility that’s both broad and deep.
Expert Insight: Monitoring is not a replacement for audits or bounties, it’s the connective tissue. It brings real-time awareness to otherwise static defenses.
What to Check: Whether the system can take predefined actions when threats are confirmed.
What to Look For: Look for options like automatic pausing of transactions, blocking known bad actors, or escalating to human intervention with rich context.
Expert Insight: In Web3, attacks move at the speed of block finality. Automation isn’t a luxury—it’s a necessity for cutting off exploits before they cascade.
Hypernative is a real-time monitoring, risk detection and automated response solution that identifies threats with high accuracy and gives customers precious minutes to respond before exploits can do damage. The platform tracks both onchain and offchain data sources and uses battle-tested, sophisticated machine learning models, heuristics, simulations, and graph-based detections to identify over 300 risk types, from smart contract hacks and bridge security incidents to frontend compromises, market manipulations and private key theft.
Reach out for a demo of Hypernative’s solutions, tune into Hypernative’s blog and our social channels to keep up with the latest on cybersecurity in Web3.
Secure everything you build, run and own in Web3 with Hypernative.
Website | X (Twitter) | LinkedIn